
Check SSL Cert
Matteo Corti created a great shell script that can be used for TLS certification that enhances Nagios monitoring tools. The repo for the project can be found at here. This script parses data from an x509 certificate that can be pulled via openSSL or stored locally. It’s a general tool that can use a multitude of different protocols, including LDAP.
Basic Certificate Expiration Check
./check_ssl_cert -H host [options]
In this example we will use www.rexconsulting.net
./check_ssl_cert -H www.rexconsulting.net
will return:
SSL_CERT OK - x509 certificate 'rexconsulting.net' from 'Let's Encrypt Authority X3' valid until Aug 2 19:59:51 2020 GMT (expires in 73 days)|days=73;;;;
The dates are matched by comparing the before and after dates on the certificate with local dates.
Certificate Expiration Check With CN Matching
There is also an option to input a string to compare with the name of the website that the certificate was issued to, known as the common name (CN). It’s strict pattern matching, so if the CN on the certificate is ‘rexconsulting.net’, then the input pattern must also be the string match ‘rexconsulting.net.’
Inputting
./check_ssl_cert -H www.rexconsulting.net -n rexconsulting.net
returns:
SSL_CERT OK - x509 certificate 'rexconsulting.net' from 'Let's Encrypt Authority X3' valid until Aug 2 19:59:51 2020 GMT (expires in 73 days)|days=73;;;;
Certificate Expiration Check With Issuer Check
This script also has the capability to input a string to compare with the issuer listed on the certificate. The issuer chain for Rex Consulting looks like this:
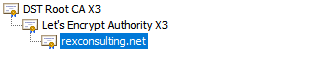
The CN of Rex Consulting’s certificate issuer is “Let’s Encrypt Authority X3”, and the CN of “Let’s Encrypt Authority X3’s” issuer is “DST ROOT CA X3.”
Issuer Check for “Let’s Encrypt Authority X3”
Inputting
./check_ssl_cert -H www.rexconsulting.net -i "Let’s Encrypt Authority X3"
returns:
SSL_CERT OK - x509 certificate 'rexconsulting.net' from 'Let's Encrypt Authority X3' valid until Aug 2 19:59:51 2020 GMT (expires in 73 days)|days=73;;;;
Issuer Check for “DST Root CA X3”
Inputting
./check_ssl_cert -H www.rexconsulting.net -i "DST Root CA X3"
returns:
SSL_CERT OK - x509 certificate 'rexconsulting.net' from 'DST Root CA X3' valid until Aug 2 19:59:51 2020 GMT (expires in 73 days)|days=73;;;;
By default check_ssl_cert will confirm the validity of the root certification by looking for its match inside /etc/pki/tls/certs on CentOS/RHEL or /etc/ssl/certs on Ubuntu.
Conclusion
Check SSL Cert is a very useful script and I’m omitting some of its additional options for the sake of brevity. If you have any questions regarding TLS or Nagios checks, don’t hesitate to leave a comment or use our Contact page.